Custom alerts and data visualization let you quickly identify and prevent Active Directory security and replication issues.
Make sure that no AD event in your Active Directory environment goes unnoticed: Active Directory auditing can track and log user access attempts to network resources regardless of whether the attempt is legitimate, accidental, or malicious.
As soon as matching event IDs are written to the Security Event Log, Paessler PRTG detects them.
Set custom warning and/or error thresholds for the sensors monitoring your Active Directory events. As soon as these thresholds are breached, PRTG notifies you via SMS, email, push notification, and other methods.
This way, you can rest assured that if PRTG doesn’t sound the alarm, everything’s running as expected.
Keep track of your Active Directory events with PRTG’s wealth of historical monitoring data. Instead of going through tons of AD log data, you can zoom in on the events that really matter. With PRTG, you can also easily generate custom reports for in-depth data analysis or get a more high-level view for the management team.
Diagnose network issues by continuously tracking Active Directory events. Show AD replication errors, changes to AD groups that can indicate a network security issue, and other key metrics in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot your entire Active Directory domain.
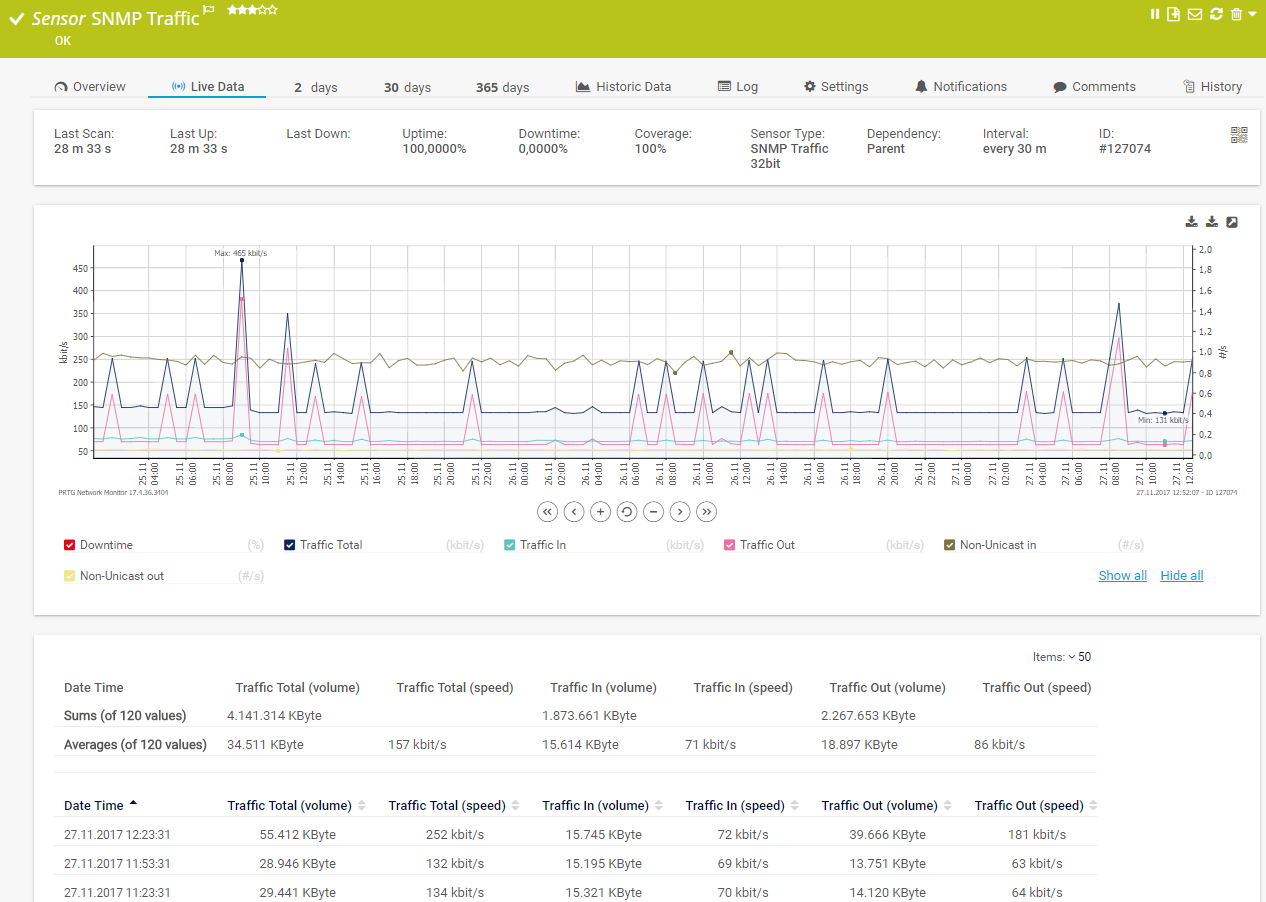
Live traffic data graph in PRTG

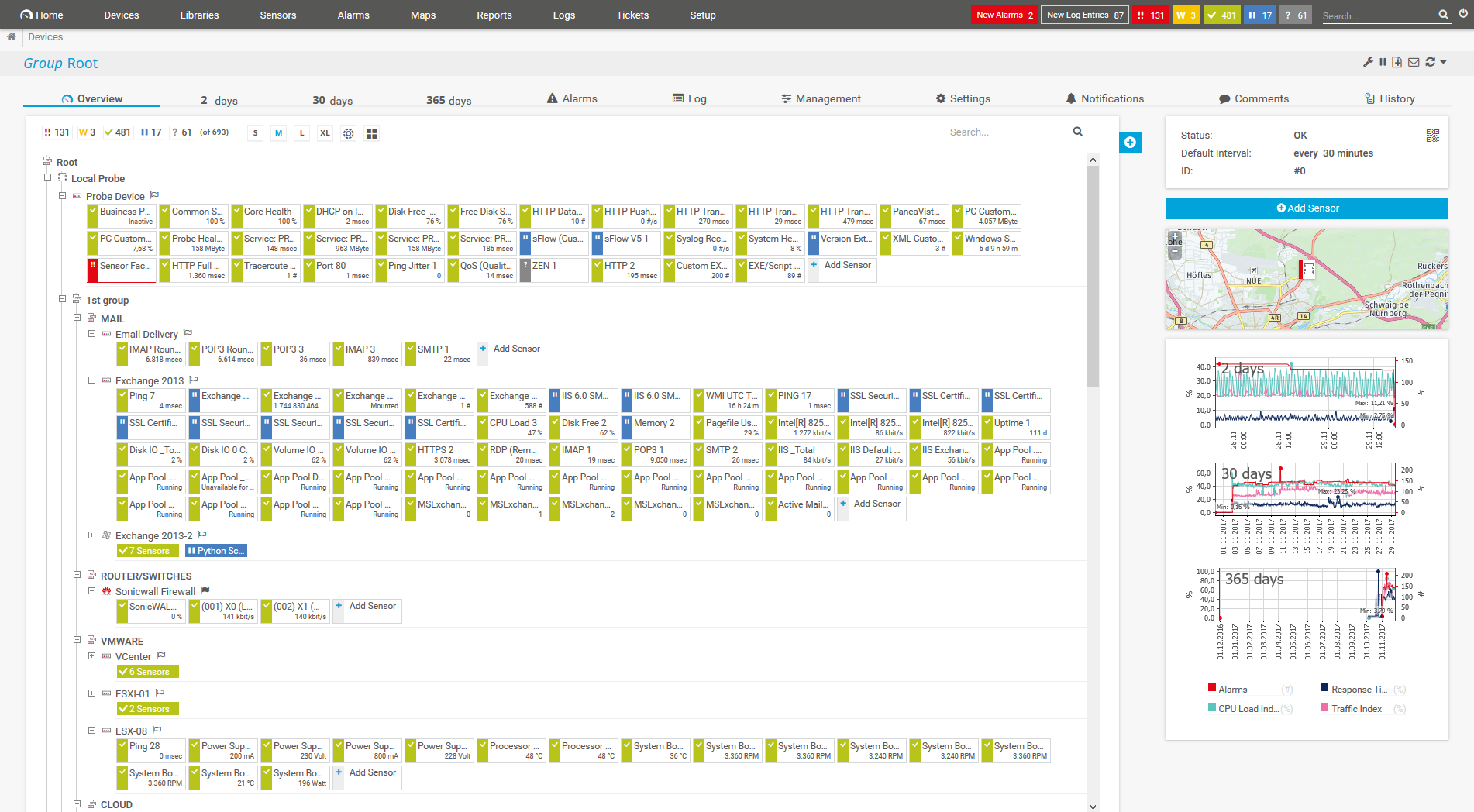
Device tree view of the complete monitoring setup
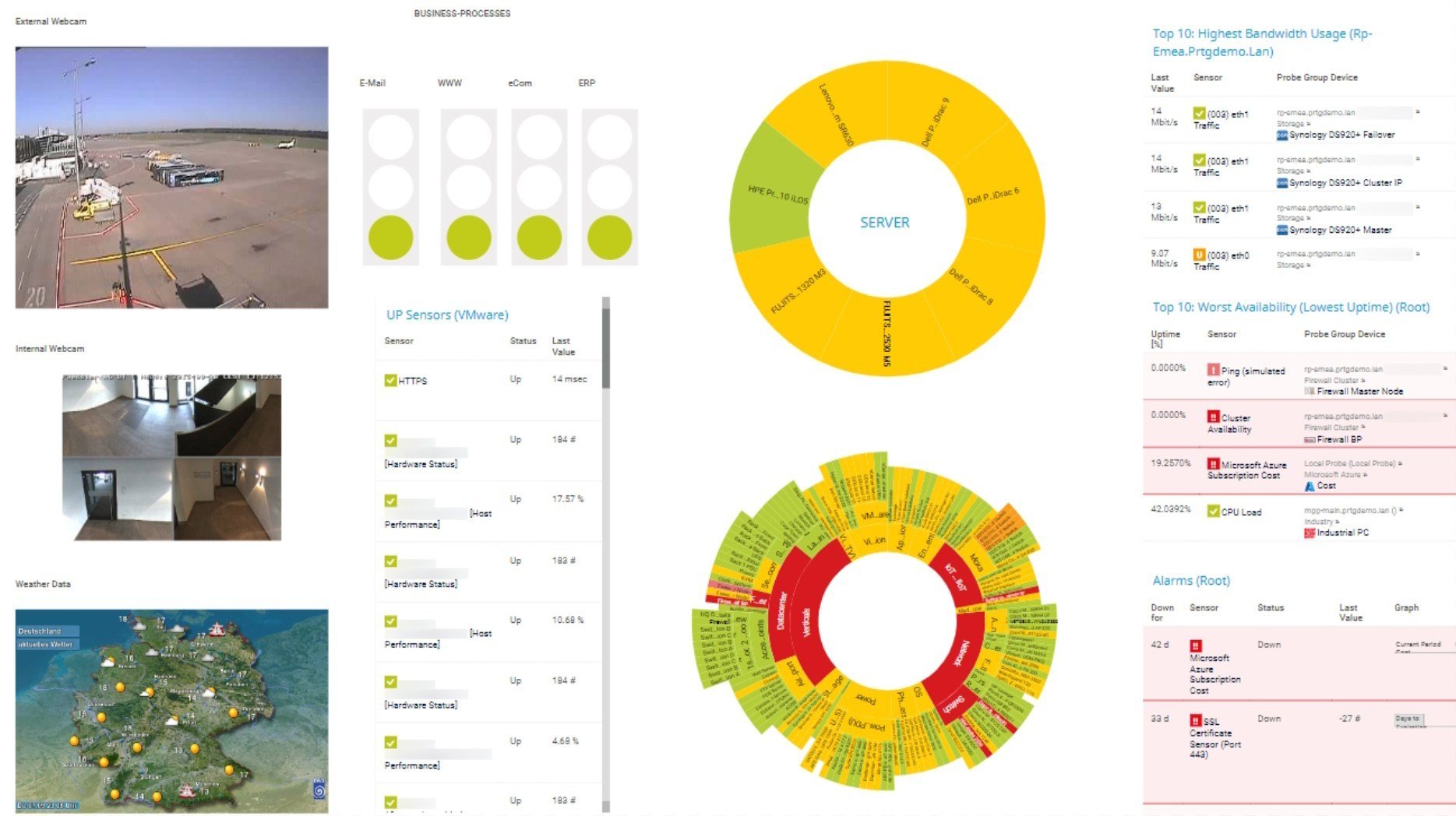
Custom PRTG dashboard for keeping an eye on the entire IT infrastructure

Live traffic data graph in PRTG

The replication of directory data between various domain controllers can be prone to error. In turn, the resulting errors can cause problems with authentication and with access control.
The preconfigured Active Directory Replication Errors v2 sensor monitors different parameters during the replication of directories and the synchronization of the various domain controllers, including the number of consecutive synchronization failures, pending replication operations, and the time of the last synchronization attempt.
Maintaining an overview of logged-out or deactivated users is nearly impossible with standard AD tools.
With PRTG, you get a ready-to-use script for the EXE/Script Advanced sensor, which searches the Active Directory for all logged-out and deactivated users, and then lists them in PRTG.
To use this script, PRTG requires the Active Directory PS module. With a Search-AD account, you can run the script with a number of different queries.
Running a ready-to-use script for the EXE/Script Advanced sensor in PRTG, you can enumerate how many people are in a group and show an error status when the number of members exceeds the intended amount.
This way, you’ll always be notified if someone joins an AD group like Domain Admins.
For AD security audits, you can set up the preconfigured Event Log (Windows API) sensor watching the Windows Security Event Log for Active Directory changes to the Domain Admin Security Group.
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Set up PRTG in minutes and use it on almost any mobile device.
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.

Paessler and Plixer provide a complete solution adding flow and metadata analysis to a powerful network monitoring tool.
IT that works constitutes a business-critical basis for a company's success. Availability and security must be defined for the respective purpose and closely monitored – by OT and IT alike.

With ScriptRunner Paessler integrates a powerful event automation platform into PRTG Network Monitor.
Custom alerts and data visualization let you quickly identify and prevent Active Directory security and replication issues.
Network Monitoring Software – Version 25.1.104.1946 (March 18th, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
Active Directory (AD) is a directory service created by Microsoft for use in a Windows Server environment. It provides authentication and authorization functions as well as a framework for other related services. The directory itself is an LDAP database that contains networked AD objects.
Active Directory auditing is the process of tracking and recording events that occur within an AD environment. This includes actions such as logins, changes to user accounts, access to files or resources, and administrative activities. Auditing helps organizations maintain security, compliance, and accountability by providing a detailed record of who did what, when, and from where within the network. Typical components of the audit process are audit policies, audit logs, and audit reports.
One of the many functions Active Directory serves is that of a gate keeper – controlling which users can use resources on the network, and their level of interaction with those resources. File shares, file servers, applications, internet access, printers: all depend on Active Directory to allow or deny access. This makes it vitally important for system administrators to keep track of how AD is protecting those resources.
Microsoft has included excellent audit facilities within AD. Log on/log off, object access, policy changes, account management, and many other activities all leave detailed records in the Windows Security Event Log. Unfortunately, even for only a small network, AD auditing can create huge numbers of log events, making it very difficult to keep track of the really important ones. Active Directory auditing tools like PRTG help you keep track of these events and alert you if something is not working as it should.
An Active Directory (AD) audit involves several critical security aspects to ensure the integrity, availability, and confidentiality of the AD environment. Here are some key security aspects typically involved in an AD audit
User account management
Password policies
Group Policy Objects (GPOs)
Access controls
Auditing and logging
Security configuration
Replication and availability
Service accounts
Security policies
Physical security
Incident response
Compliance and reporting
No. PRTG is proprietary network monitoring software that lets you keep an eye on your entire IT infrastructure, including:
If you use Microsoft Entra ID (formerly Azure AD) and want to keep an eye on what’s happening there, we’ve got you covered as well.
Set up, for example, a Microsoft Azure Subscription Cost sensor to keep your subscription costs in check. Or create a custom PRTG sensor for monitoring activities that might pose a risk:
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.