OT cybersecurity strategy monitoring with PRTG
Continuously check your OT network for risks and ensure its security
- Identify and resolve OT network anomalies proactively
- Monitor security-relevant components and systems 24/7
- Receive custom alerts and notifications in real time
PRTG OT cybersecurity strategy monitoring: What you’ll find on this page
Unbreak security breaches with the help of OT network monitoring
It’s no longer recommended to isolate OT environments from the outside world as a security strategy. IT/OT convergence, the digitalization of OT networks, the need to give equipment vendors remote access, and the need to collect, analyze, and store sensor data from IIoT applications all require industrial networks to be connected to external systems or devices.
And that means: They are vulnerable to attack.
That is why monitoring forms a crucial part of any Operation Technology (OT) cybersecurity strategy. Paessler PRTG monitoring software can help make your industrial IT infrastructure more secure.
PRTG makes OT network monitoring as easy as it gets
Custom alerts and data visualization let you quickly identify and prevent OT security issues.
5 reasons why PRTG is the perfect complement to your OT cybersecurity strategy
There are various strategies for keeping OT networks safe and secure, and PRTG can play an important role in each.
Detect network anomalies in real time
Sudden spikes in bandwidth usage. Unusual traffic. Unexpected new connections. These are just some examples of typical anomalies – or deviations from the norm – that could possibly indicate malicious activity in a network.
Use PRTG to understand what is “normal” in your network, then define alerts and notifications that are triggered when thresholds are exceeded. This way you are alerted in time to anomalies and potentially suspicious activity in your network.
Ensure in-depth defense mechanisms
Several segmented layers of defense can help to keep the core OT network safe. Network segmentation, where the OT network is either separated from the IT network by an industrial demilitarized zone, or where the OT network itself is separated into several zones, are also defense-in-depth strategies.
Monitoring with PRTG can form a critical part of a defense-in-depth approach by watching over the industrial firewalls, the interfaces between segments, and other potential risks like open ports.
Complement IPS & IDS systems
Industrial Intrusion Prevention Systems (IPS) and Intrusion Detection Systems (IDS) are both deep-packet-inspection methods used to keep OT networks safe. These systems either prevent an intrusion or trigger a notification when anomalous data is discovered.
Use OT network monitoring with PRTG alongside IPS and IDS solutions to provide a full picture of what’s happening in your IT/OT infrastructure.
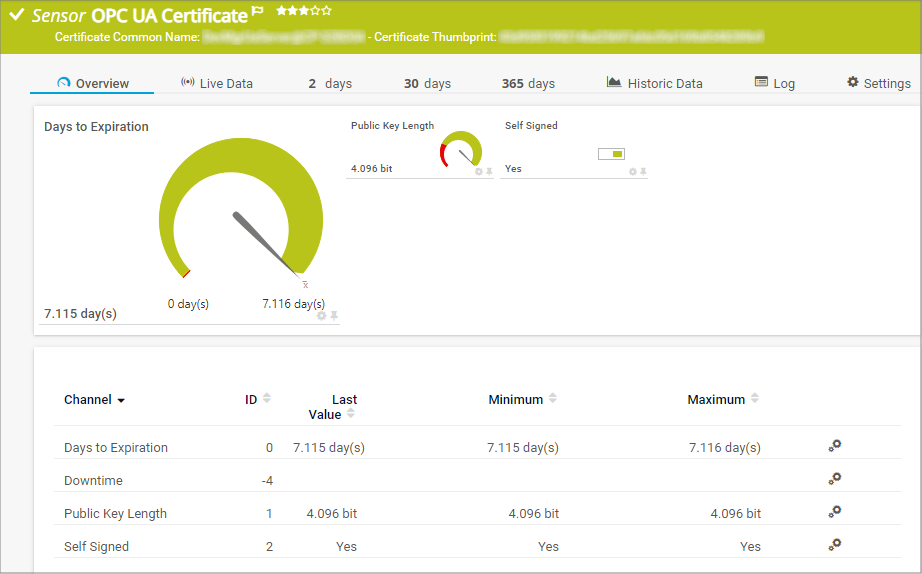
Get OPC UA monitoring included
OPC UA is a common standard in industrial environments, and checking for unusual OPC UA activity in a network is a good way of spotting a cyberattack. Additionally, OPC UA employs certificate-based X.509 encryption, and the certificates should be constantly monitored to ensure their validity.
PRTG can check for unusually large numbers of rejected OPC UA calls or sessions in a network, which might indicate malicious activity. It also monitors OPC UA certificates throughout the OT environment to ensure that they are valid.
Keep an eye on industrial firewalls
When it comes to security in any network, firewalls are key, and it’s no different for OT networks. PRTG helps you keep your industrial firewalls safe by monitoring the availability and status of the firewall as well as ingoing and outgoing traffic.
Our monitoring software is compatible with countless manufacturers such as Rhebo, Fortinet, Cisco, and others. In the case of issues, PRTG triggers automatic alerts and notifies you via SMS, email, or push notification before more serious problems occur.
What OT network security monitoring looks like in PRTG
Diagnose network issues by continuously tracking your IT, OT, and IIoT networks. Show cybersecurity risks such as hacker, malware, and ransomware attacks in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot disruptions in production and business processes, as well as supply chains.
Start monitoring for improved OT cybersecurity with PRTG and see how it can make your network more reliable and your job easier.
How to protect your OT infrastructure physically, with PRTG
OT security practices are not only about cybersecurity detection and mitigation. It’s about the physical security of your factory buildings and production lines, too. PRTG helps you in various ways to prevent unauthorized access and hazards such as fire and water damage.
CCTV monitoring
IP camera systems consist of multiple components: surveillance cameras, video recorders, power supplies, and network and data transmission systems.
PRTG helps you watch the watchers by continuously monitoring the availability, health, and performance of your entire CCTV system.
IoT monitoring
IoT sensors are commonly used to monitor environmental conditions on the factory floor, such as temperature, humidity, vibration levels, voltage and more, as well as access to doors or windows.
Using SNMP, MQTT, and other technologies, PRTG retrieves data from IoT devices and alerts you as soon as there is an issue.
Find the root cause of the problem with our PRTG OT monitoring solution
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
PRTG is compatible with all major vendors, products, and systems
Check out PRTG in an industrial environment
PRTG is monitoring software that can keep an eye on the health, status, and condition of all kinds of components across IT, OT, and IIoT:
- Enjoy out-of-the-box support for common industrial standards and protocols – OPC UA, MQTT, Modbus, and more
- Visualize your environment on custom, centralized dashboards
- Get data from industrial gateways about the factory floor and the industrial Internet of Things
- Monitor industrial ethernet devices in your OT environment
- Extend the functionality of common industrial security solutions
- Get automated, customizable alerts and notifications when values exceed predefined thresholds
PRTG integrates with well-known industrial security software

Rhebo and PRTG offer a comprehensive monitoring solution for IT and OT environments: from condition monitoring through to anomaly and threat detection.

Moxa is a leading manufacturer of network devices for industrial environments. Together, MXview software by Moxa and PRTG allow for the monitoring of industrial ethernets.
Get your free white papers
White paper I
In modern industrial IT, the right teams need the right data. Our guide shows how to implement holistic monitoring that brings elements from IT, OT and IIoT into your dashboards.
White paper II
Our second guide gives you inspiration and ideas for dashboards that feature IT, OT and IIoT data – all in one place. We show you what truly convergent industrial dashboards look like!
PRTG makes OT network monitoring as easy as it gets
Custom alerts and data visualization let you quickly identify and prevent OT security issues.
“Excellent tool for detailed monitoring. Alarms and notifications work greatly. Equipment addition is straight forward and server initial setup is very easy. ...feel safe to purchase it if you intend to monitor a large networking landscape.”
Infrastructure and Operations Engineer in the Communications Industry, firm size 10B - 30B USD
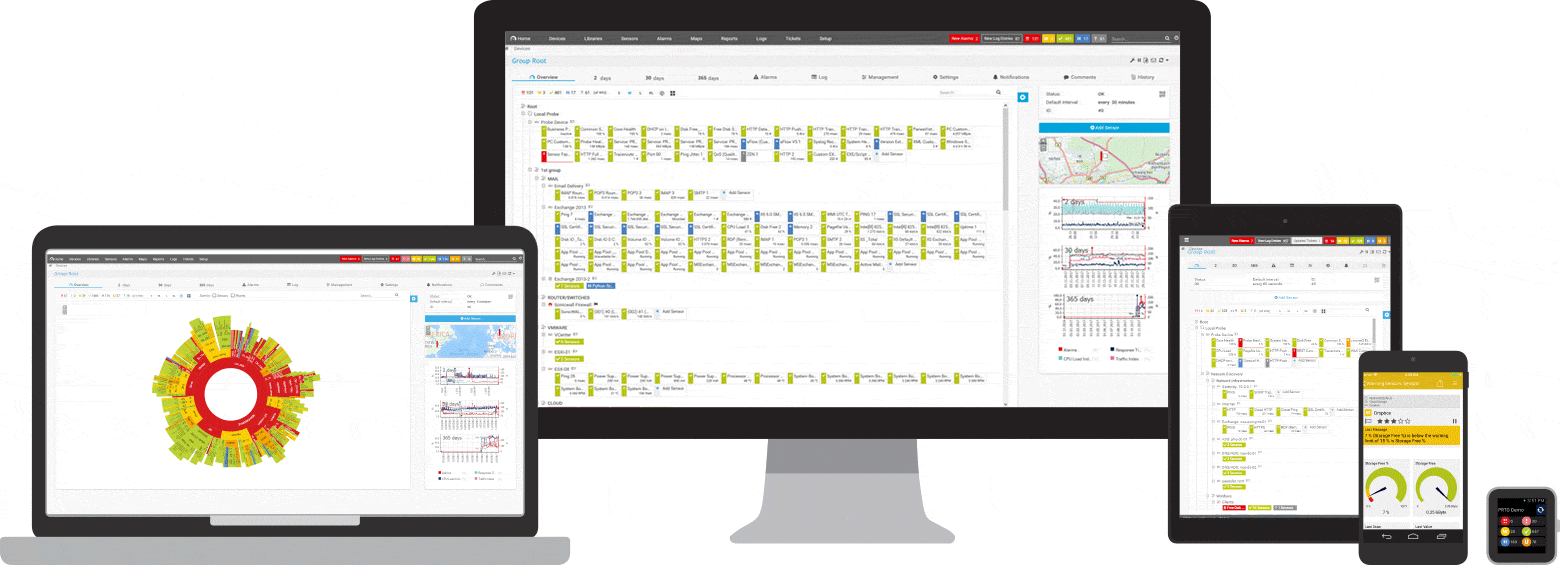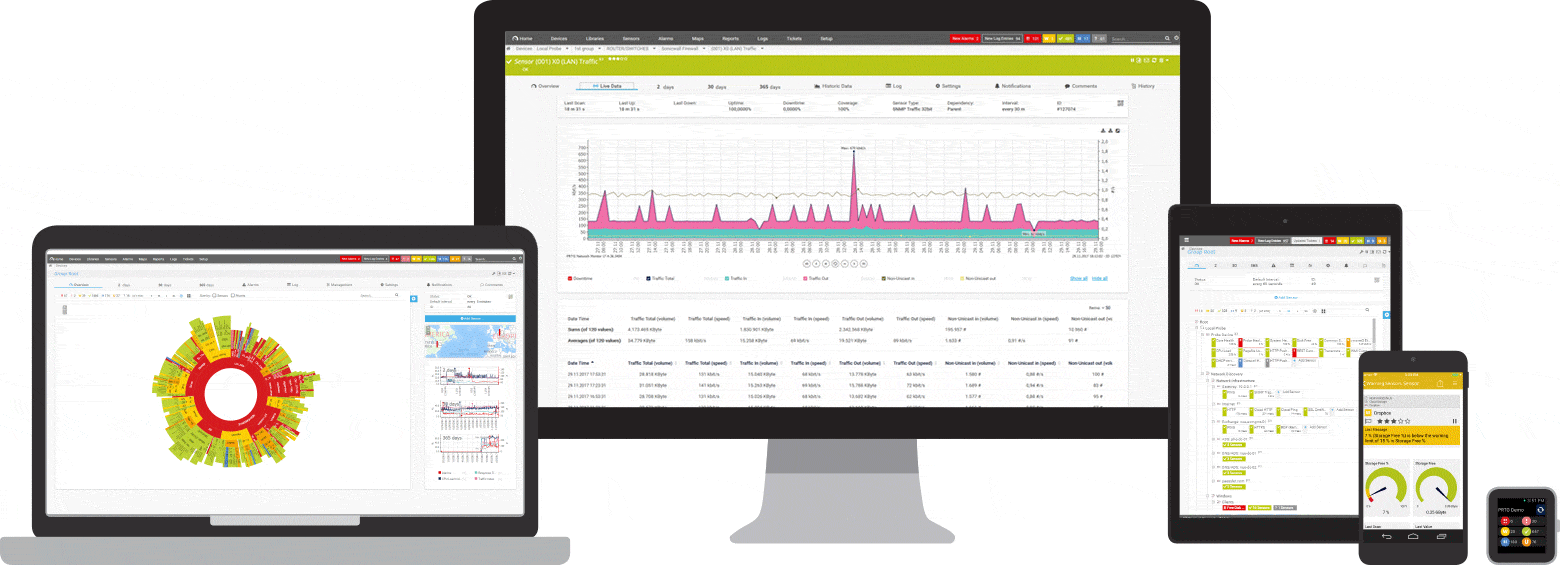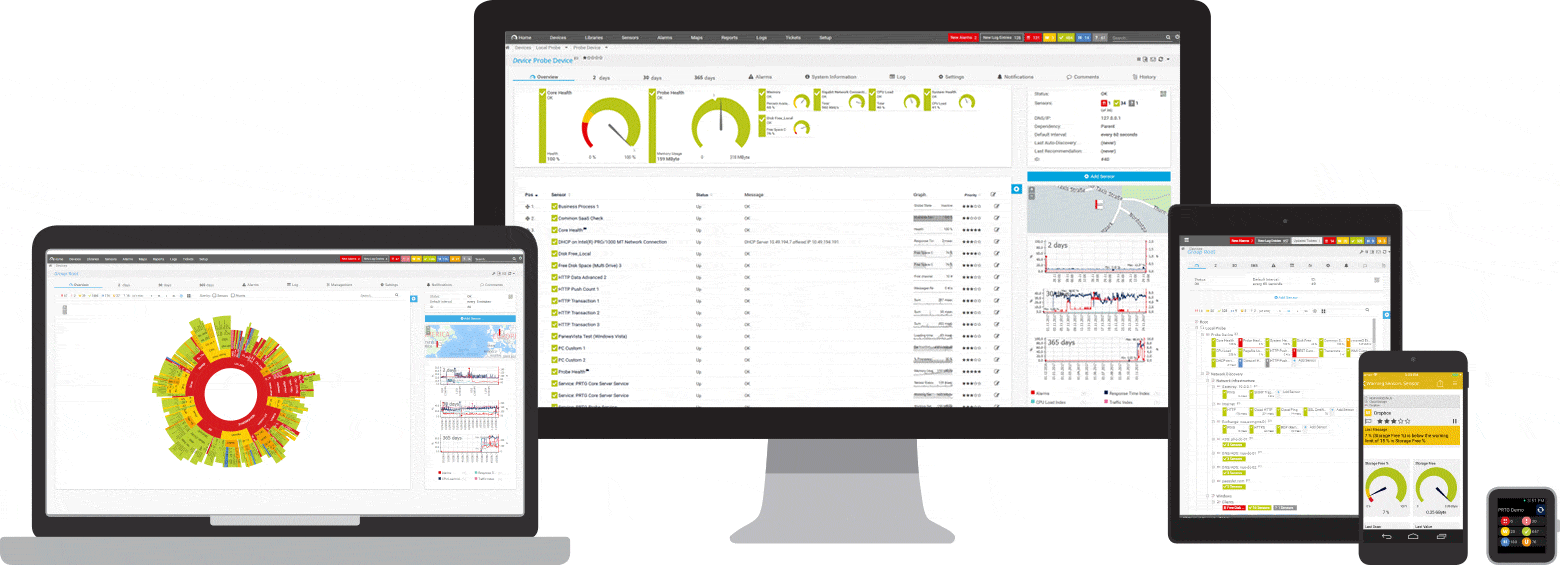
Your OT network monitor at a glance – even on the go
Set up PRTG in minutes and use it on almost any mobile device.

Find the root cause of the problem with our PRTG OT monitoring solution
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
PRTG: The multi-tool for sysadmins
Adapt PRTG individually and dynamically to your needs and rely on a strong API:- HTTP API: Access monitoring data and manipulate monitoring objects via HTTP requests
- Custom sensors: Create your own PRTG sensors for customized monitoring
- Custom notifications: Create your own notifications and send action triggers to external systems
- REST Custom sensor: Monitor almost everything that provides data in XML or JSON format
We asked: would you recommend PRTG?
Over 95% of our customers say yes!
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins.
The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Still not convinced?
More than 500,000
sysadmins love PRTG
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Monitor your entire IT infrastructure
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Try Paessler PRTG
for free
Everyone has different monitoring needs. That’s why we let you try PRTG for free.
Start monitoring for improved OT cybersecurity with PRTG and see how it can make your network more reliable and your job easier.
|
PRTG |
Network Monitoring Software - Version 25.2.106.1114 (May 6th, 2025) |
|
Hosting |
Download for Windows and cloud-based version PRTG Hosted Monitor available |
Languages |
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese |
Pricing |
Up to 100 sensors for free (Price List) |
Unified Monitoring |
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more |
Supported Vendors & Applications |
|