Custom alerts and data visualization let you quickly identify and prevent IP traffic issues.
Many IP sniffers on the market let you analyze individual IP packets, but without the full network overview provided by Paessler PRTG. These tools give you detailed information on the data that is carried in each respective packet (packet capture) and discover any suspicious data traffic in the network, but they lack insight into other areas of your infrastructure.
Network monitoring tools like PRTG let you monitor your entire wireless and local network, including its hardware, applications, virtual machines, network traffic, and more. You can keep an eye on bandwidth and filter your traffic by type, protocol, source, and destination. PRTG’s built-in alarm system immediately notifies you of potential issues so that you can act in time.
Diagnose network issues by continuously tracking and analyzing IP data traffic. Show packet header analysis and other key metrics in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot problems in your IT infrastructure.
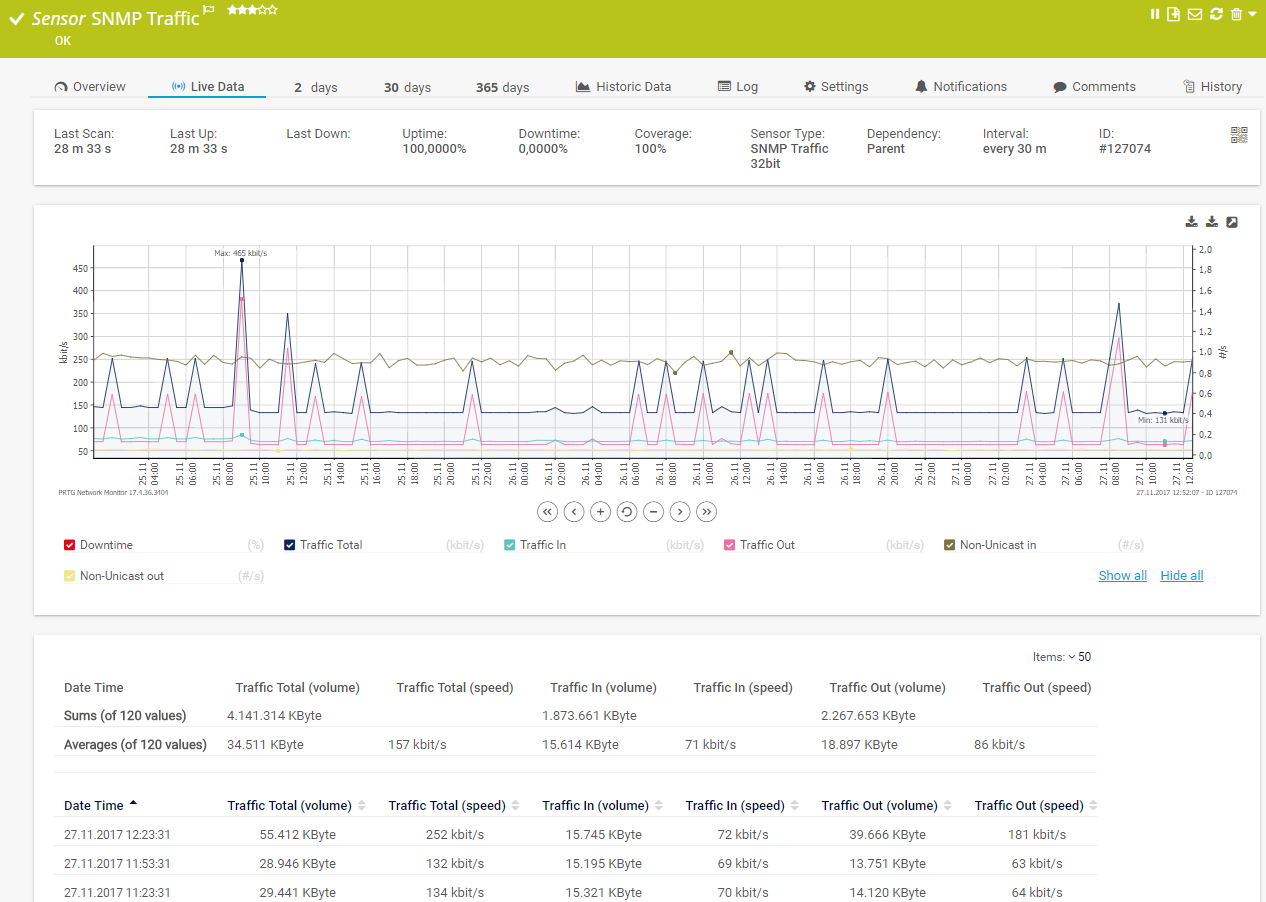
Live traffic data graph in PRTG
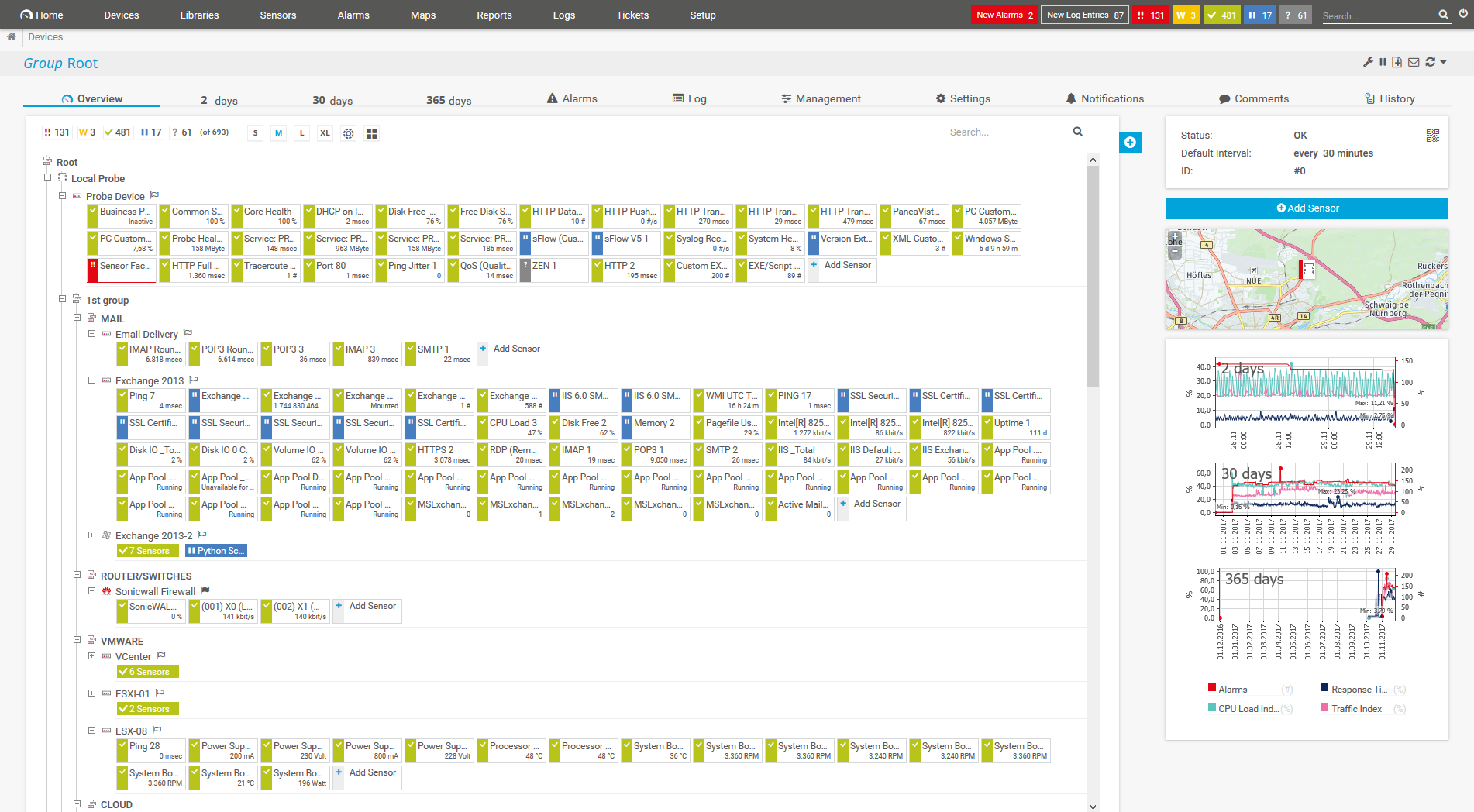
Device tree view of the complete monitoring setup
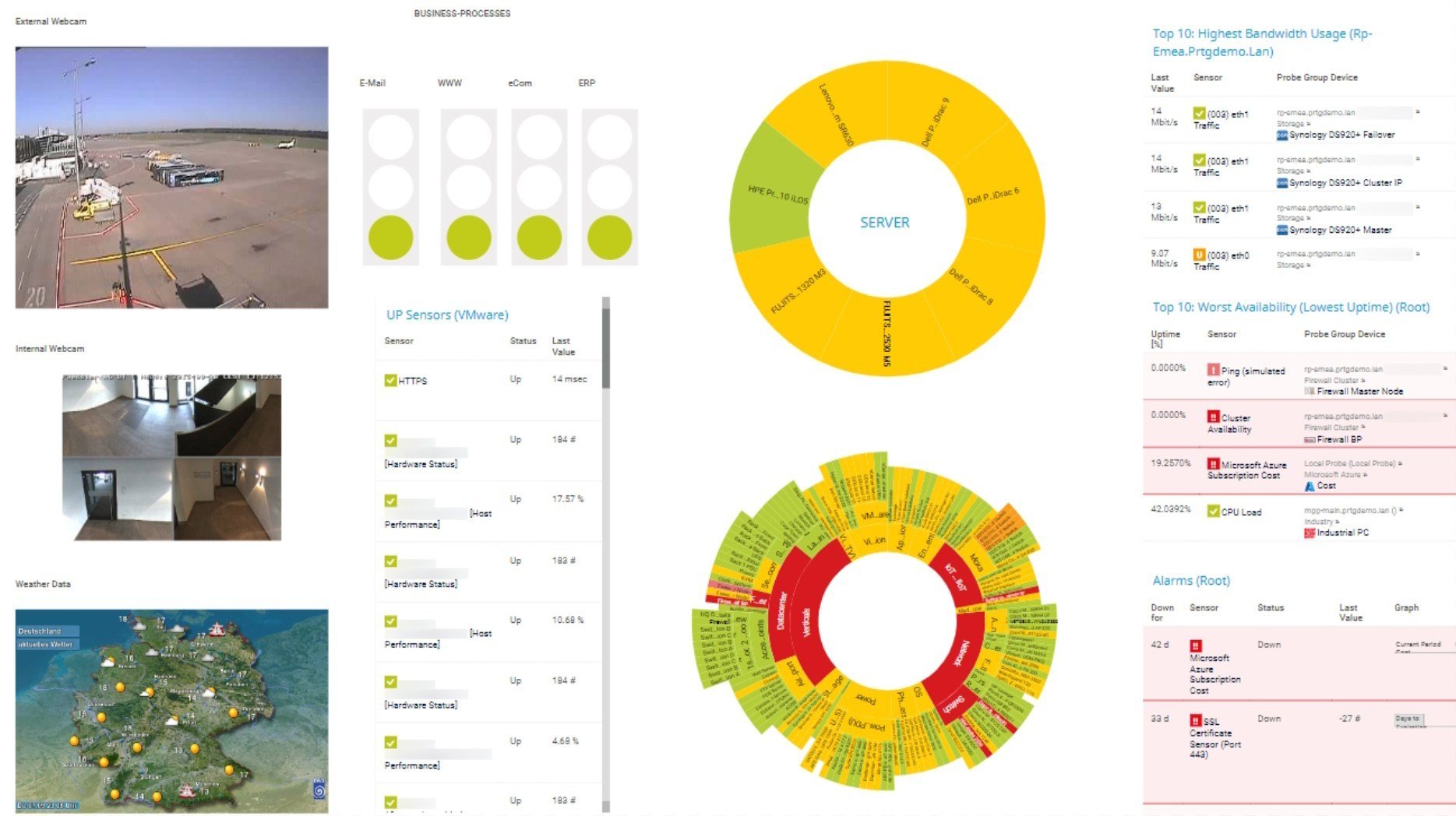
Custom PRTG dashboard for keeping an eye on the entire IT infrastructure

Live traffic data graph in PRTG

Device tree view of the complete monitoring setup
PRTG comes with more than 250 preconfigured sensors for monitoring your entire IT infrastructure, including packet sniffing, flow monitoring, and traffic monitoring via SNMP. You can also easily create custom sensors using the PRTG API.
The Packet Sniffer sensor monitors your traffic, then filters it by IP address, protocol, and connection. It also analyzes the headers of incoming and outgoing data packets. All this IP packet analysis data is presented on customizable graphs and so-called toplists.
PRTG monitors all the major flow protocols (IPFIX, NetFlow, jFlow, sFlow). As with the Packet Sniffer sensor, you can break down your traffic by IP address, protocol, and port to take a closer look. The NetFlow protocol is used mostly by Cisco devices, which you can monitor with our NetFlow v5 and NetFlow v9 sensors (preconfigured or custom).
The SNMP Traffic sensor monitors traffic on a device using the Simple Network Management Protocol. It shows the number of incoming and outgoing errors, discarded packets, unicast and non-unicast packets; the incoming, outgoing, and total traffic; and the number of incoming unknown protocols.
You can use IP tracking with PRTG to resolve a specific problem, for example getting to the root of a short-term spike in traffic and find out if the problem lies with hardware resources, VPN connectivity, or with the internet service provider (ISP).
You can also use IP sniffing with PRTG to plan and develop your network infrastructure. It keeps a constant eye on your entire network, using historical data logs and lookups to recognize long-term trends.
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Custom alerts and data visualization let you quickly identify and prevent IP traffic issues.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
“Excellent tool for detailed monitoring. Alarms and notifications work greatly. Equipment addition is straight forward and server initial setup is very easy. ...feel safe to purchase it if you intend to monitor a large networking landscape.”
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
With ScriptRunner Paessler integrates a powerful event automation platform into PRTG Network Monitor.
Siemon and Paessler bring together intelligent building technology and advanced monitoring and make your vision of intelligent buildings and data centers become reality.
UVexplorer integrates tightly with PRTG to bring fast and accurate network discovery, detailed device inventory, and automatic network mapping to the PRTG platform.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.1.104.1946 (March 18th, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
IP sniffing, also known as packet sniffing or network sniffing, is the practice of intercepting and examining data packets flowing across a computer network. This technique is often used for troubleshooting network issues, but it can also be exploited for malicious purposes, such as capturing sensitive information like usernames and passwords. Unauthorized IP sniffing b ymalware or other attacks is generally considered a security risk and can violate privacy.
A sniffer is a tool or program that inspects data traffic on network devices. Incoming and outgoing data traffic is “sniffed” as it passes through network interfaces. Sniffers log data packets and use IP addresses to identify senders and recipients.
The difference between an IP sniffer and an IP puller lies primarily in their methods, functions, and typical use cases. An IP sniffer is a powerful network analysis tool, while an IP puller is more narrowly focused on identifying and extracting IP addresses, often with questionable intent.
An IP sniffer is a type of network monitoring tool used to capture and analyze network traffic. It operates at a low level in the network stack, allowing it to intercept and examine data packets as they travel across a network. These tools are often referred to as "packet sniffers" or "network sniffers."
An IP sniffer captures all or selected packets of data traveling through a network. Each packet contains various information, including the source and destination IP addresses, protocols, and potentially the content of the data.
After capturing the packets, the sniffer can analyze them to reveal details about network activity, such as which devices are communicating, the nature of the data being transferred, and the IP addresses involved.
IT admins use sniffers to diagnose network issues, such as identifying bottlenecks, misconfigurations, or unauthorized devices. Security experts use sniffers to detect suspicious activity, such as potential intrusions or data exfiltration. Developers and researchers use sniffers to study how different network and internet protocols operate or to debug network applications.
An IP puller (or IP grabber) is a tool specifically designed to extract or "pull" the IP address of a specific user, often without their knowledge. It is generally used in more targeted ways and is frequently associated with unethical or malicious activities.
An IP puller might involve social engineering, such as tricking a user into clicking a link or interacting with content that captures their IP address. Unlike a sniffer, an IP puller focuses on identifying the IP address of a particular individual or device. IP pullers typically work with specific applications, such as online games, chat services, or social media platforms, where they can intercept or log the IP addresses of connected gamers or users.
Some people use IP pullers to find the IP addresses of others to carry out Distributed Denial of Service (DDoS) attacks or to harass them online. In some cases, IP pullers are used to track URLs or a user's online activity, or they track IP addresses and geolocations without their consent.
The difference between an IP sniffer and an IP catcher lies in their methods, scope, and typical use cases. Both involve the identification of IP addresses, but they operate in distinct ways and are used for different purposes. An IP sniffer is a comprehensive network tool used for capturing and analyzing all traffic on a network, including IP addresses. In contrast, an IP catcher is a more targeted tool that captures IP addresses when users interact with specific online resources.
An IP sniffer is a tool used to capture and analyze network traffic. It operates at a lower level in the network stack, intercepting all data packets as they travel across a network. The sniffer can capture a wide range of information beyond just IP addresses, including data content, protocol details, and other metadata.
An IP catcher is a tool or method designed to capture the IP address of a user who interacts with a specific resource, such as a website, link, or online service. Unlike an IP sniffer, an IP catcher typically operates at a higher level and is focused on recording IP addresses from specific interactions rather than capturing all network traffic.
An IP catcher logs the IP address of a user when they visit a specific website, click on a link, or access a resource controlled by the person using the catcher. This is done through embedded scripts, tracking pixels, or web server logs. The IP catcher records the IP address and possibly other information (like browser type or location) of users who interact with the monitored resource.
Common use cases include tracking visitors to a website to understand where traffic is coming from (web analytics), monitoring and logging access to a service or website to detect suspicious behavior, or analyzing the reach and engagement of shared links or online campaigns in marketing.
If you have a critical problem – such as unusually high network traffic or trouble transmitting data – an IP sniffer will help you uncover the cause. IP sniffers can even be used to sniff the traffic itself (i.e. individual data packets). The PRTG Packet Sniffer sensor monitors traffic around the clock, including the distribution of traffic across devices, applications, and IP addresses.
When you run PRTG for the first time, the Auto-Discovery feature will be launched automatically. Simply enter a range of IP addresses. PRTG will add all the devices (servers, routers, switches, firewalls, etc.) within this range to your monitoring environment. You can then create the Packet Sniffer sensor separately on the server whose traffic you wish to monitor, or via the monitoring port of your switch if you wish to include all traffic in your monitoring.
The terms “IP scanner” or “network scanner” are often used synonymously with “IP sniffer.” However, IP scanners are mostly used to scan operating systems such as Windows, Mac, or Linux, while IP sniffing tools are used more globally.
An IP logger is a tool or service designed to capture and record the IP addresses of users who interact with a specific link, website, or piece of content. The primary function of IP logging is to log the IP address of a visitor when they access or click on something controlled by the person using the IP logger.
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.