Custom alerts and data visualization let you quickly identify and prevent security threats and unauthorized access.
Using PRTG for cybersecurity monitoring gives you the confidence to protect your entire IT infrastructure from emerging threats. Imagine being able to effortlessly identify vulnerabilities before they become breaches, while having real-time visibility into network traffic and suspicious activity. PRTG not only alerts you to potential threats, but helps you act quickly - preventing costly downtime and ensuring business continuity.
Monitor your network with PRTG for suspicious activity, allowing you to act before cyber threats escalate.
Generate detailed reports on network vulnerabilities, incidents, and security posture to share with stakeholders and enhance decision-making.
Visualize critical data on cybersecurity risks and threats in user-friendly, customizable dashboards that offer clear insights.
Whether you're monitoring a small business or a complex IT environment, PRTG scales to fit your cybersecurity needs.
Diagnose network issues by continuously tracking security threats and vulnerabilities. Show network activity, unauthorized access attempts and other key metrics in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot potential cyber-attacks.
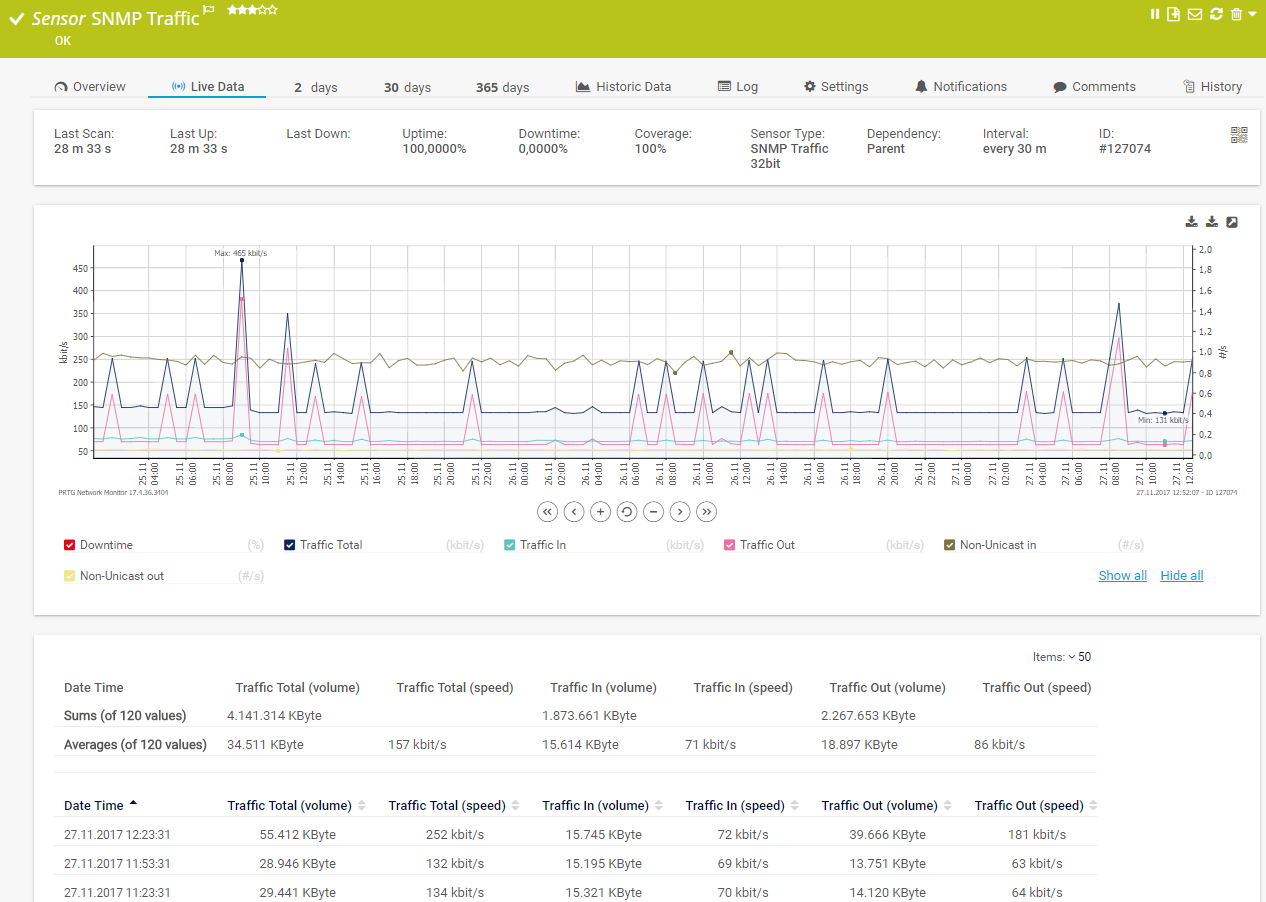
Live traffic data graph in PRTG
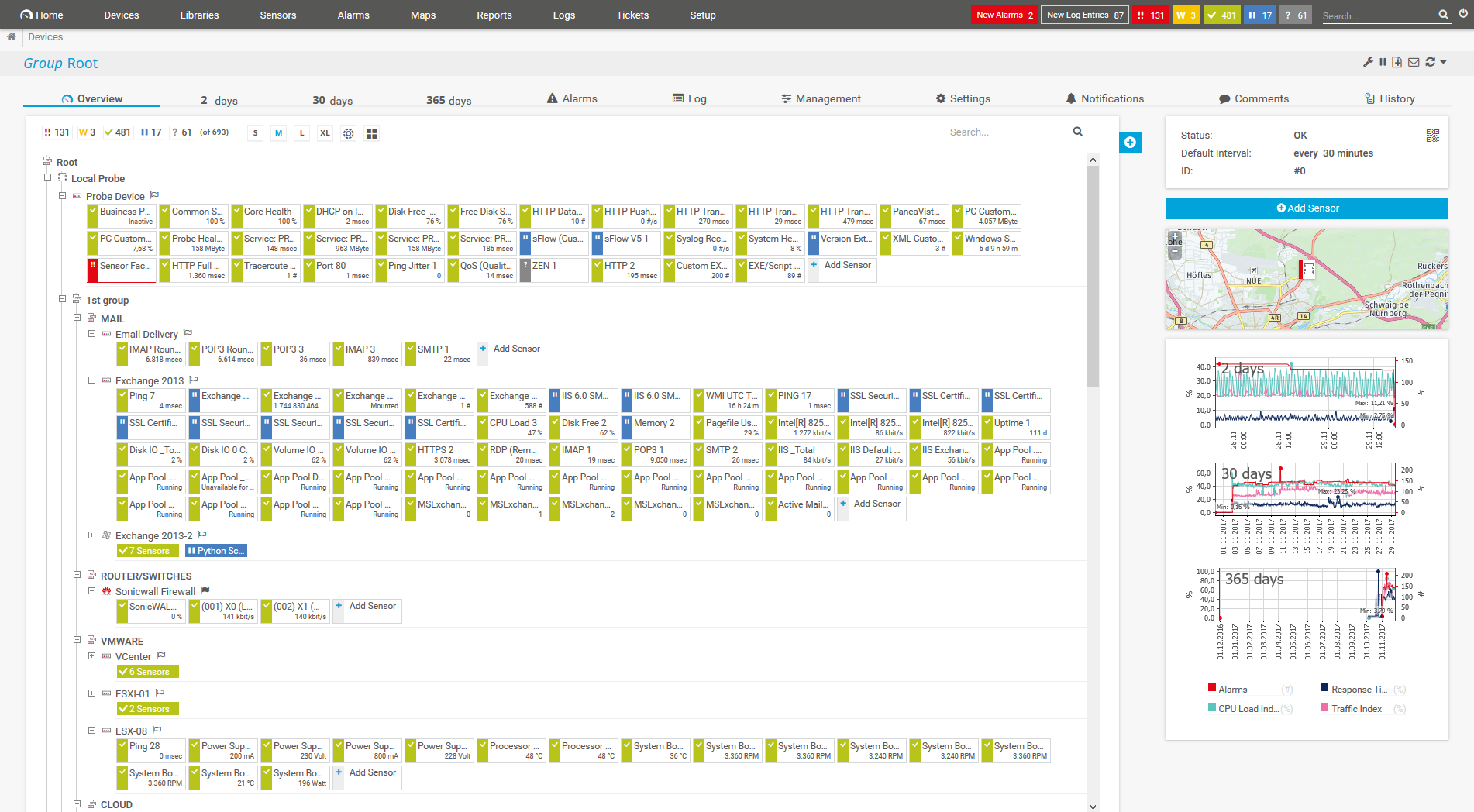
Device tree view of the complete monitoring setup
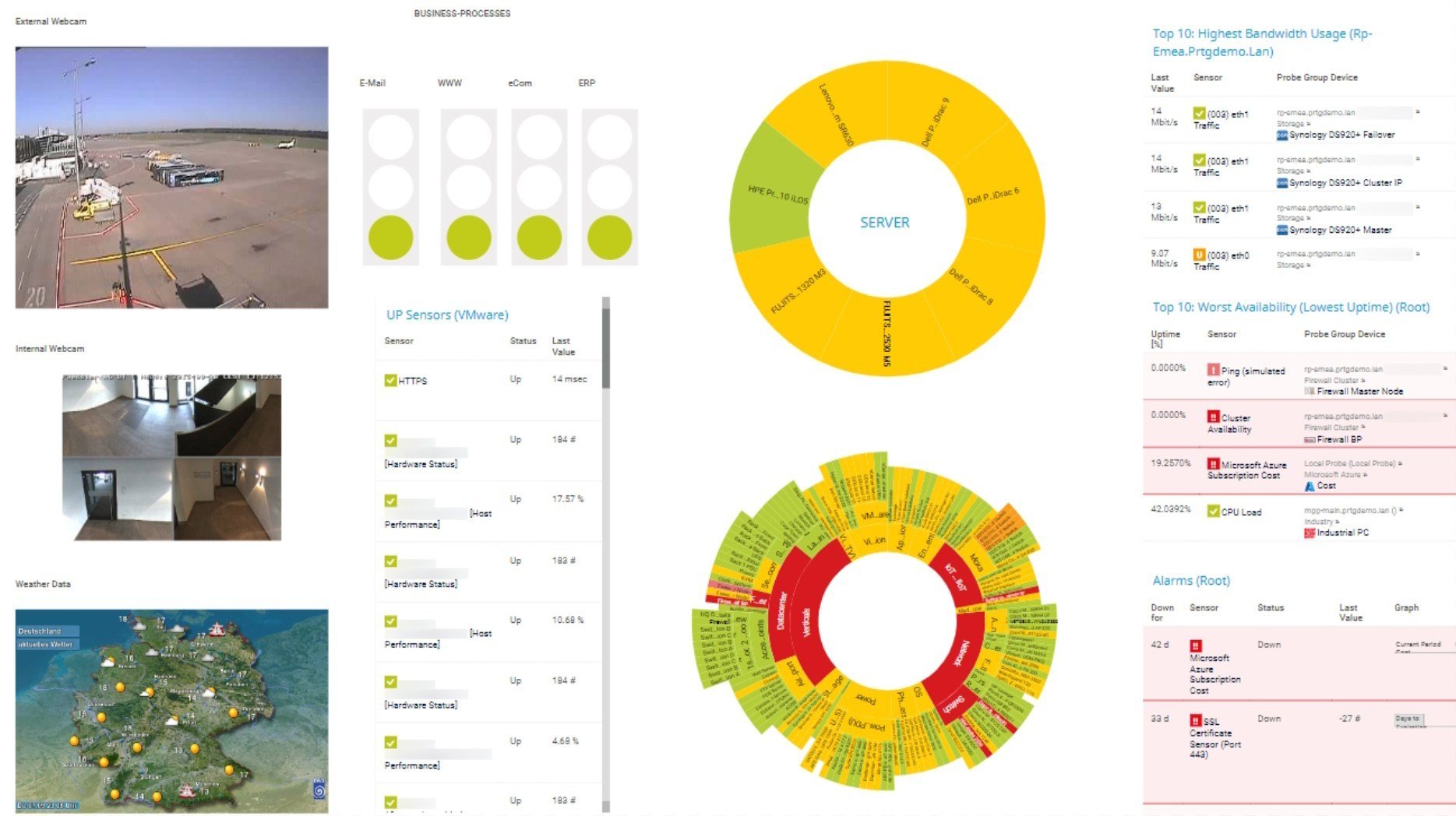
Custom PRTG dashboard for keeping an eye on the entire IT infrastructure

Live traffic data graph in PRTG

Device tree view of the complete monitoring setup
PRTG offers flexible subscription plans that fit your business needs, whether you're a small business or a large enterprise. With no long-term commitments or hidden fees, you can adjust your plan as your infrastructure grows or changes, ensuring that you only pay for what you need.
Expect excellent support from a team of network monitoring experts. From setup to troubleshooting, their guidance will keep your system running smoothly and give you peace of mind that your network is always protected.
PRTG provides an easy-to-use interface that simplifies even the most complex cybersecurity monitoring tasks. With minimal training, you can quickly get up to speed, making it easy to manage your security posture and respond to threats efficiently, no matter the size of your team.
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.

As a member of the Cisco Partner Program, Paessler is one of the market leaders that enhances the Cisco technology portfolio with products that are proven to easily integrate with Cisco devices.
What does this mean for you?
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
Axis offers one of the most complete and reliable product portfolios, an expanded professional network, and comprehensive integration support for video management software.
Monitor all major physical hazards in IT rooms and racks such as critical climate factors, fire or burglary.
Asset visibility is a big problem for many IT teams. Not having an accurate inventory of tech assets is inefficient, costly and a potential security risk.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
A cybersecurity monitoring tool tracks network activity, detects vulnerabilities, and identifies potential cybersecurity threats in real time. These tools automate threat detection and help security operations teams respond quickly. They monitor for malware, unauthorized access, and cyber criminals, helping prevent cyber risk such as data breaches and security incidents. By analyzing log data and user behavior, these tools provide actionable insights for remediation and protection.
PRTG offers robust cybersecurity monitoring with real-time alerts for suspicious activity, such as unauthorized access and potential malware attacks. It helps discover and address vulnerabilities across your network while tracking endpoint monitoring metrics like laptops and other mobile devices. By integrating with threat intelligence tools, PRTG can alert you to cybercrime early and reduce false positives by filtering out legitimate alerts for a more focused response.
Yes, PRTG supports continuous monitoring and real-time analysis to detect and respond to security incidents. It covers your entire attack surface, from endpoints to network devices, while offering insights into cyber risk. PRTG integrates with penetration testing tools to proactively identify weaknesses and follows NIST standards to ensure compliance and improve your overall security posture.
PRTG automates threat detection by analyzing log data and monitoring network traffic for signs of malware or suspicious activity. It works alongside intrusion detection systems and firewalls to protect your infrastructure from cyber criminals. Real-time alerts from PRTG help security teams respond quickly to reduce risk. With built-in remediation tools, you can take immediate action to prevent further escalation.
Our monitoring solution tracks critical cybersecurity metrics such as network traffic, firewall activity, and endpoint monitoring to detect threats and vulnerabilities. It provides observability into potential security issues, logs network and user activity, and visualizes key data. The ability of PRTG to monitor a variety of systems, including laptops and remote devices, ensures comprehensive security across your entire IT infrastructure.
PRTG combines ease of use with powerful features, like real-time threat detection and customizable reports on security metrics. It automates many security tasks, reducing the workload for you and security teams. PRTG is a reliable choice for cyber risk monitoring due to its flexibility, support for SIEM tools and integration with threat intelligence systems. With its scalable infrastructure, PRTG is ideal for businesses of any size looking to protect their attack surface and ensure quick remediation of potential threats.
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.