SSH monitoring with PRTG
Check mission-critical Unix network components securely
- Monitor macOS, Linux, and other Unix-based devices through Secure Shell
- Keep an eye on the health and performance of your SAN
- Get automatically alerted about performance issues with custom notifications
PRTG makes SSH monitoring as easy as it gets
Custom alerts and data visualizations let you quickly identify and prevent Linux server availability and performance issues
Greater security doesn’t mean less usability
It's hard to beat SSH for security.
But if your organization's network uses various Windows Server versions as well as macOS and Linux systems, and other Unix network devices – and, let's face it, that's the case in most organizations – the number of different monitoring tools you'll need to have in place can quickly reach a hair-tearing level of complexity.
The whole point of network monitoring tools is that they should make your life easier, not harder. Which is why we've designed Paessler PRTG to be as simple and intuitive as it gets.
Whether your devices support SSH, SNMP, or another protocol, our monitoring environment brings together all your data in one place, giving you a single, unified view of your network's health, and taking the effort out of ensuring it stays fast, stable, and reliable.
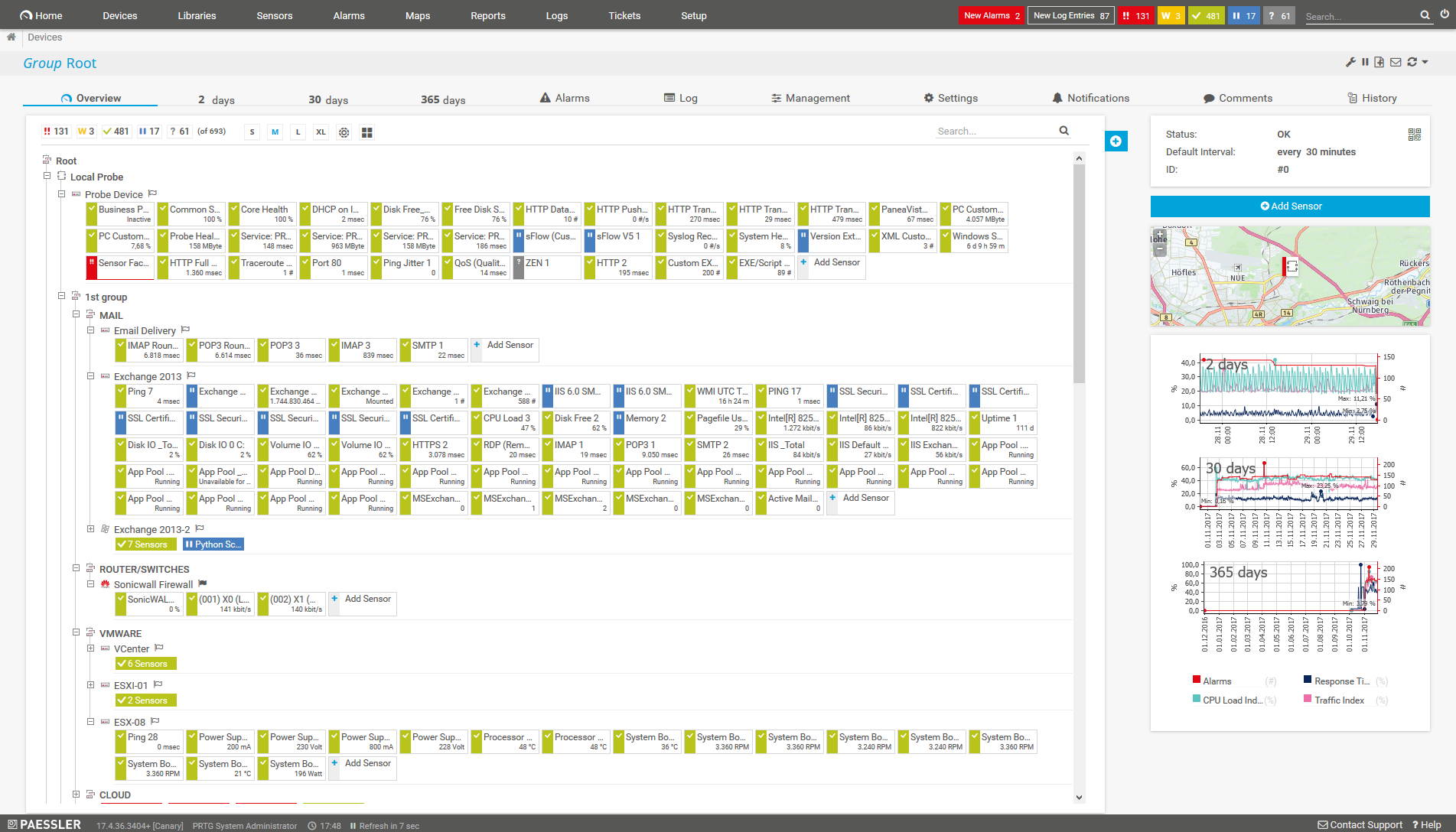
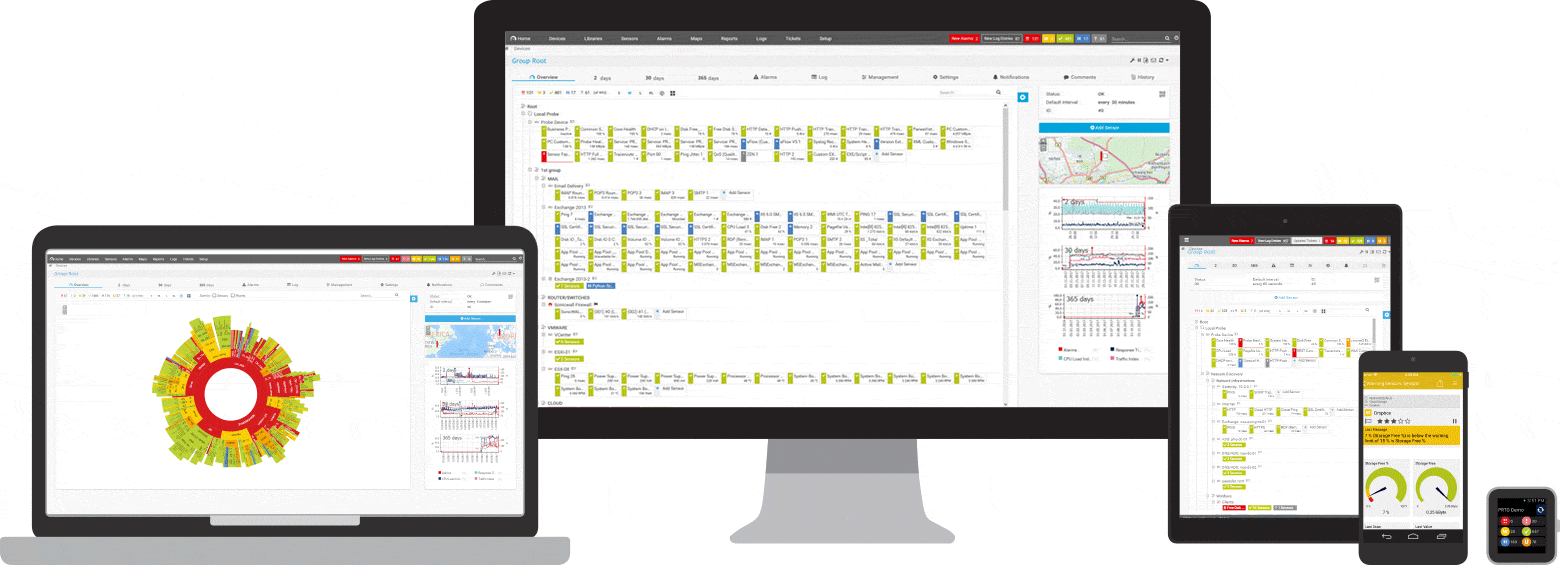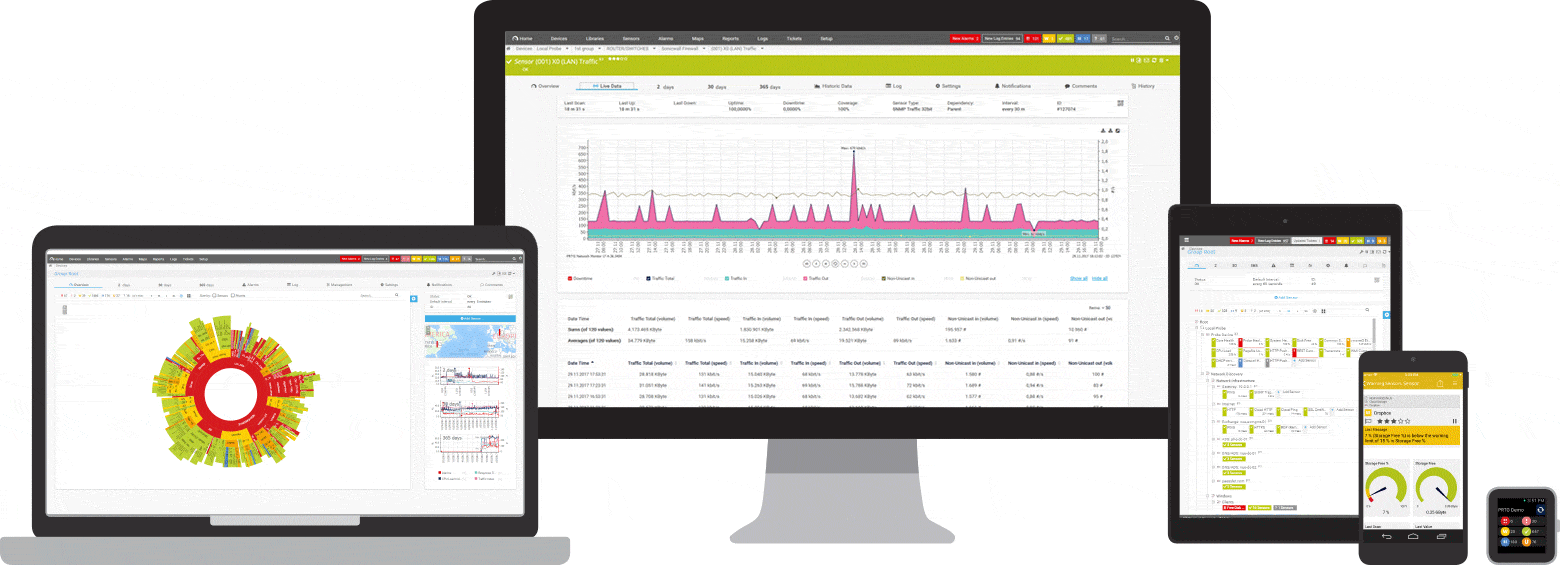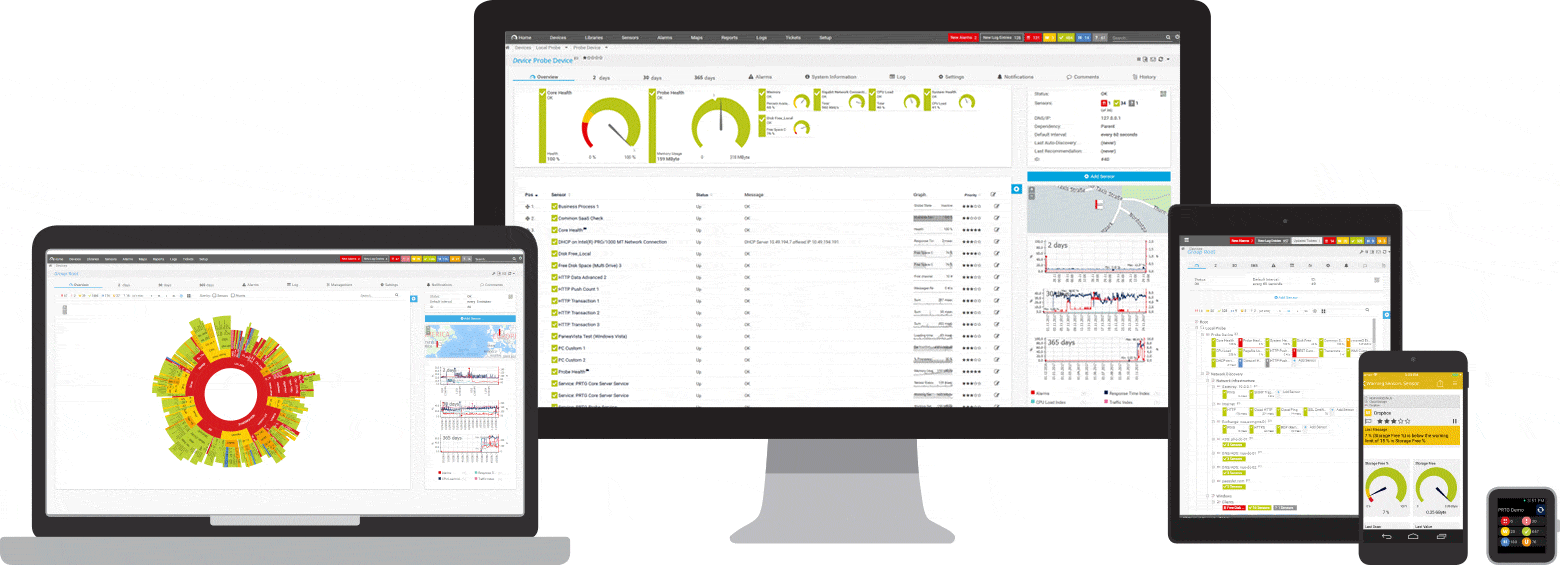
What SSH monitoring looks like in PRTG
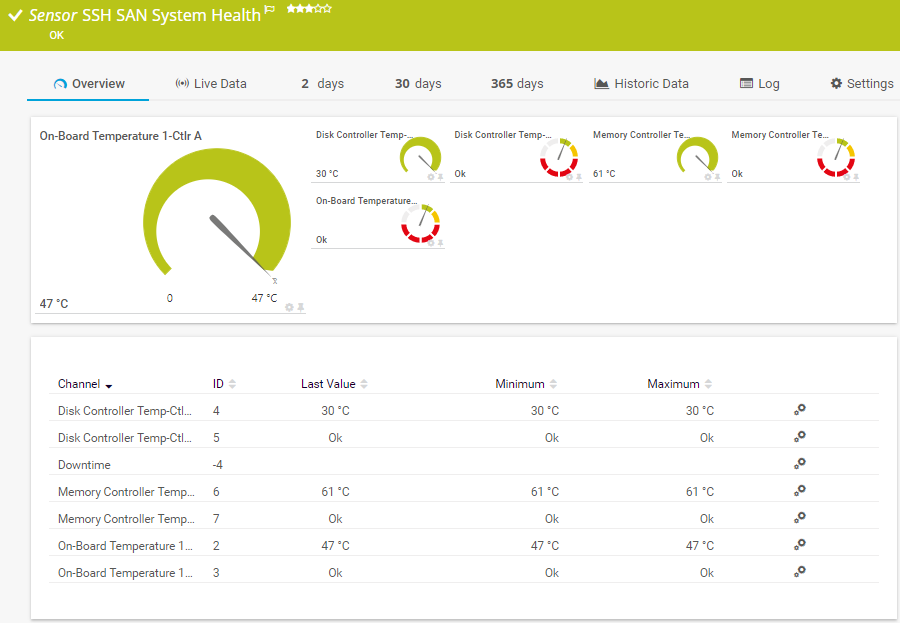
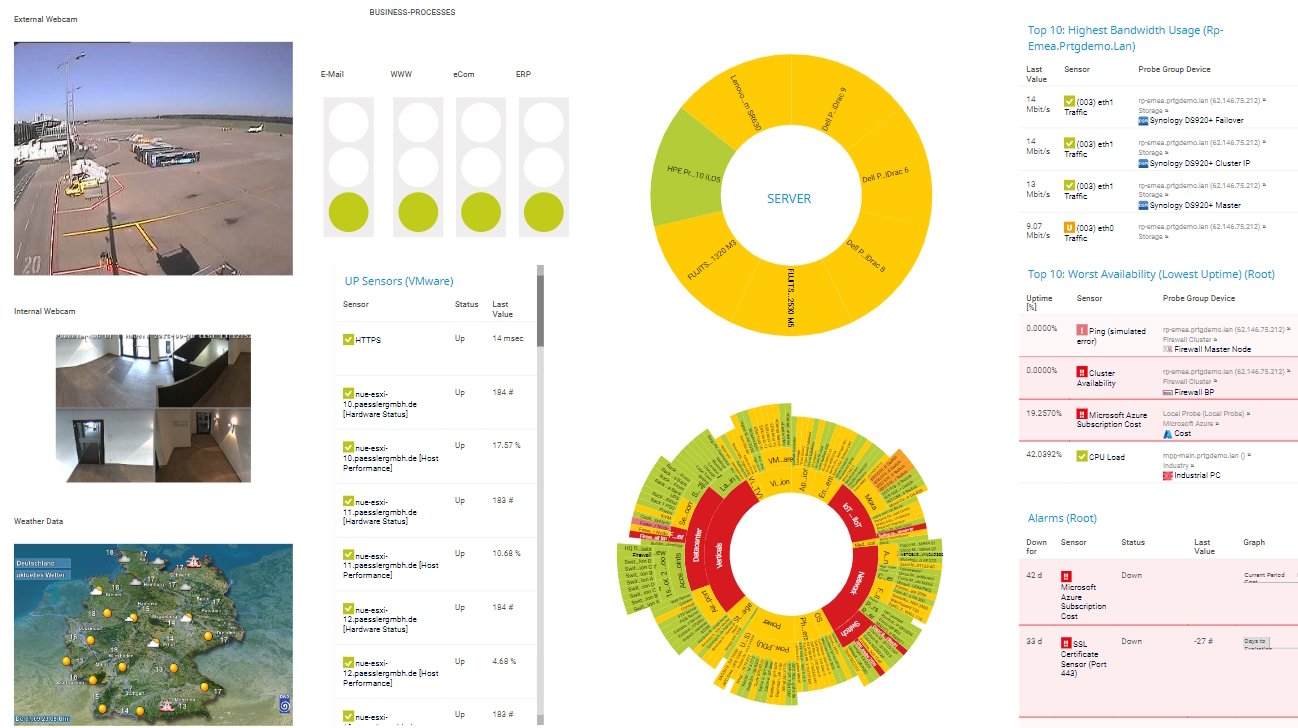
Diagnose network issues by continuously tracking FTP servers, storage area networks (SAN), and Linux network components. Show response time, disk space, system health, and other key metrics in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot low availability, high memory load, lack of disk space, and more.
Start monitoring via SSH with PRTG and see how it can make your network more reliable and your job easier.
4 reasons why to choose PRTG as your SSH monitoring tool
Effortless setup
No need to fiddle about with device settings. Or, worse, install software on every device you want to monitor. Our agentless monitoring software comes with an automatic network discovery that will detect the devices, establish your SSH connection, and even set up the appropriate sensors for you.
Complete visibility
Availability. Performance. Operating system status. Memory. Server load. With a range of SSH-native sensors and the ability to create your own, PRTG can track every variable you can think of, and present the data in a format anyone can understand.
Speedy troubleshooting
Zoom in on problems promptly, before they spiral out of control. Once you pick your preferred thresholds, PRTG watches them like a hawk and alerts you using customizable notification templates if your device risks going under or over. Which means fewer disruptions and a shorter to-do list.
Secure data traffic
Keep track of important health stats, without putting your organization at risk. PRTG's SSH sensors support all major encryption algorithms and authentication cyphers, so unauthorized individuals won't be able to make sense of your data, even if they manage to intercept it.
Find the root cause of the problem with our PRTG SSH monitoring solution
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
PRTG is compatible with all major vendors, products, and systems
How to monitor your network using Secure Shell
Connected a device to PRTG using its IP address or DNS name? PRTG comes with many preconfigured sensors for SSH monitoring out of the box.
- The SFTP Secure File Transfer Protocol sensor monitors the response time of Linux and Unix FTP servers using FTP over SSH.
- The SSH SAN System Health, SSH SAN Physical Disk, SSH SAN Logical Disk, and SSH SAN Enclosure sensors keep a close eye on your storage area networks' physical and logical disks, system status, I/O operations, transferred data, and hardware health parameters such as voltage or temperature.
- The SSH Remote Ping checks the connectivity, response time, and packet loss between Linux or macOS and other devices using ICMP, echo requests, and SSH.
- The SSH Meminfo sensor monitors memory use on Linux and Unix systems.
- The SSH Load Average sensor monitors Linux and Unix systems' load averages.
- The SSH INodes Free and SSH Disk Free sensors monitor free index nodes and free disk space on Linux, Unix, and macOS system disks.
-
Can't find what you need? Write your own.
Create a script via the PRTG API that returns a numerical value, XML file, or JSON file from the device you want to monitor and track it using the SSH Script sensor. Or use SSH Script Advanced if you want to track multiple channels.
PRTG makes SSH monitoring as easy as it gets
Custom alerts and data visualizations let you quickly identify and prevent Linux server availability and performance issues.
“Excellent tool for detailed monitoring. Alarms and notifications work greatly. Equipment addition is straight forward and server initial setup is very easy. ...feel safe to purchase it if you intend to monitor a large networking landscape.”
Infrastructure and Operations Engineer in the Communications Industry, firm size 10B - 30B USD
Create innovative solutions with Paessler’s partners
Partnering with innovative vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
UVnetworks
UVexplorer integrates tightly with PRTG to bring fast and accurate network discovery, detailed device inventory, and automatic network mapping to the PRTG platform.
Find the root cause of the problem with our PRTG SSH monitoring solution
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
PRTG: The multi-tool for sysadmins
Adapt PRTG individually and dynamically to your needs and rely on a strong API:- HTTP API: Access monitoring data and manipulate monitoring objects via HTTP requests
- Custom sensors: Create your own PRTG sensors for customized monitoring
- Custom notifications: Create your own notifications and send action triggers to external systems
- REST Custom sensor: Monitor almost everything that provides data in XML or JSON format
We asked: would you recommend PRTG?
Over 95% of our customers say yes!
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins.
The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Still not convinced?
More than 500,000
sysadmins love PRTG
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Monitor your entire IT infrastructure
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Try Paessler PRTG
for free
Everyone has different monitoring needs. That’s why we let you try PRTG for free.
Start monitoring via SSH with PRTG and see how it can make your network more reliable and your job easier.
|
PRTG |
Network Monitoring Software - Version 25.1.104.1961 (April 7th, 2025) |
|
Hosting |
Download for Windows and cloud-based version PRTG Hosted Monitor available |
Languages |
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese |
Pricing |
Up to 100 sensors for free (Price List) |
Unified Monitoring |
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more |
Supported Vendors & Applications |
|